Tokens are essential in the developing world of cryptocurrencies and blockchain technology because they enable several tasks in decentralised ecosystems. Utility and security tokens are the two main types of these digital currencies. Despite their initial similarities, utility and security tokens have diverse uses and are governed by various regulatory frameworks. This blog examines the main distinctions between security and utility tokens and offers examples highlighting each one unique quality.
For those interested in learning more about the broader financial market including the intersection of traditional and digital assets a Stock Trading Course can provide valuable insights. Additionally understanding the various Types of Cryptocurrency is crucial for navigating this evolving landscape.
Table of Contents
- Understanding Utility Tokens
- Understanding Security Tokens
- Key Differences Between Utility Tokens and Security Tokens
- Conclusion
Understanding Utility Tokens
Definition and Purpose
Digital assets called utility tokens are made to grant users access to certain goods or services on blockchain based platforms. They are meant to be tools that let people engage with the platform’s features not investments. Utility tokens are frequently used in ecosystems to unlock features, pay for services, and encourage involvement.
Characteristics of Utility Tokens
- Functional Access: Utility tokens give their owners access to features or services on a blockchain network. They serve as a conduit for communication within the ecosystem.
- Non-Investment Nature: Since the value of these tokens is derived from their use on the platform rather than from any underlying assets or income sources they are usually not regarded as investments.
- Regulatory Considerations: Although this can vary by location utility tokens often come under less regulatory scrutiny than security tokens.
Examples of Utility Tokens
- Binance Coin [BNB]: It is the cryptocurrency exchange’s native token. BNB covers the costs of trading commissions, user discounts, and token sales on the Binance Launchpad.
- Chainlink (LINK): LINK pays for data feeds and services inside the decentralised Oracle network. It encourages data suppliers to provide smart contracts with accurate and trustworthy data.
- Filecoin (FIL): Within the Filecoin decentralised storage network, storage space and retrieval services are paid for Filecoin. Renting out their empty storage space allows users to earn FIL.
Understanding Security Tokens
Definition and Purpose
Digital Securities known as security tokens represent ownership of an underlying asset such as stock, debt, or real estate. These tokens are intended to provide features and advantages similar to those found in conventional securities such as voting rights, dividend payments, and interest payments. In addition to offering investors a clear and safe means to retain and exchange assets security tokens are frequently used to raise money.
Characteristics of Security Tokens
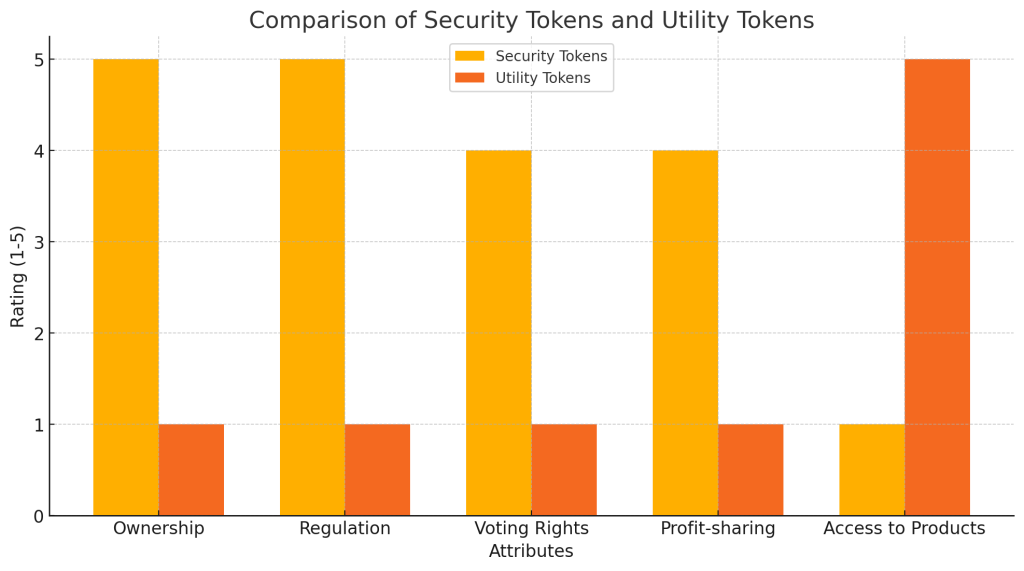
- Investment Nature: Security tokens are often backed by tangible assets and are classified as investments. Their worth is determined by how well the underlying asset performs.
- Regulatory Compliance: Security tokens must abide by stringent legal and regulatory criteria since securities rules govern them. This entails following investor protection rules and registering with regulatory agencies.
- Ownership Rights: Security token owners are entitled to certain ownership rights such as dividends, profit sharing, and voting rights within the issuing company.
Examples of Security Tokens
- TZERO [TZROP]: The platform for trading tokenised securities is called TZERO. Based on the performance of the business holders of TZROP are entitled to dividends and represent equity in the tZERO firm.
- Harbour [HBR]: Harbour makes it easier to issue security tokens secured by real estate. Tokens reflecting ownership in different real estate holdings are available for purchase by investors who will receive returns based on property appreciation and rental income.
- Polymath (POLY): It offers a security token creation and management platform. It provides a range of instruments and facilities to guarantee compliance to legal requirements empowering enterprises to tokenise their resources safely and transparently.
Key Differences Between Utility Tokens and Security Tokens
Purpose and Functionality
- Utility Tokens: They serve a primarily utilitarian purpose in a particular platform or ecosystem. They can be used to pay for purchases, gain access to services, or encourage involvement.
- Security Tokens: They are intended to provide investment opportunities and represent ownership in an underlying asset. They grant holders privileges like voting and dividends comparable to traditional securities.
Regulatory Framework
- Utility Tokens: Utility tokens within the regulatory framework are generally subject to less regulatory scrutiny, though this might vary depending on the circumstances. Since they are not considered securities most governments do not require them to abide by securities laws.
- Security tokens: They are subject to strict regulations including registration with securities regulators and abiding by rules protecting investors. Issuers are required to uphold tight legal requirements and provide complete openness.
Value Proposition
- Utility Tokens: Their usefulness on a given platform determines their worth. The platform’s uptake and the benefits that users derive from it fuel demand for utility tokens.
- Security Tokens: The performance of the underlying asset determines its worth. Like with traditional investments, investors purchase security tokens with the hope of receiving returns dependent on the asset’s performance.
Examples
- Utility Tokens: Binance Coin, Chainlink , and Filecoin
- Security Tokens: Polymath, Harbour, and tZERO
Conclusion
Professionals working in the cryptocurrency and blockchain industries must be aware of the differences between utility and security tokens. Security tokens offer investment options supported by real assets, while utility tokens offer beneficial advantages within specific platforms. Both kinds of tokens are essential in the developing digital economy, but they have different value propositions and functions in various legal environments. For more information visit The Knowledge Academy.